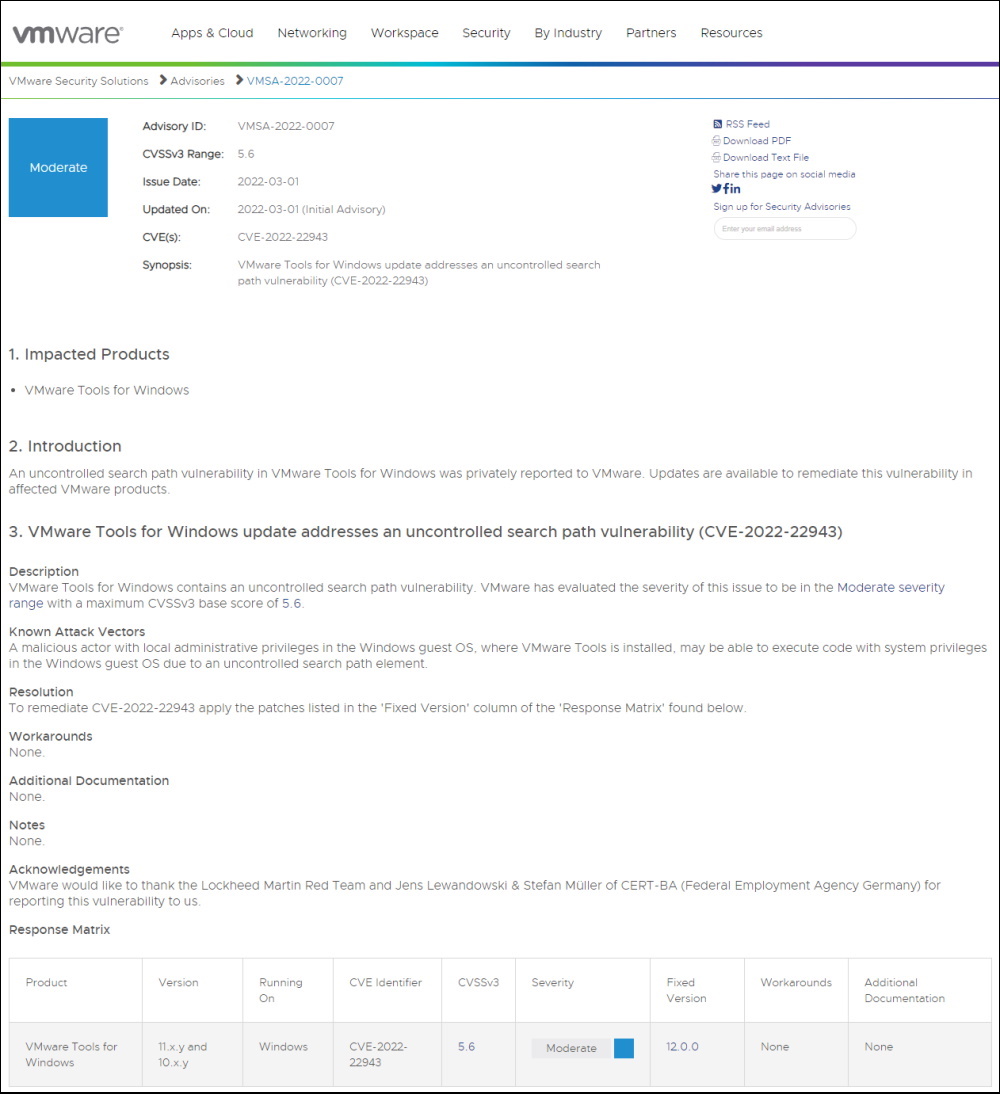
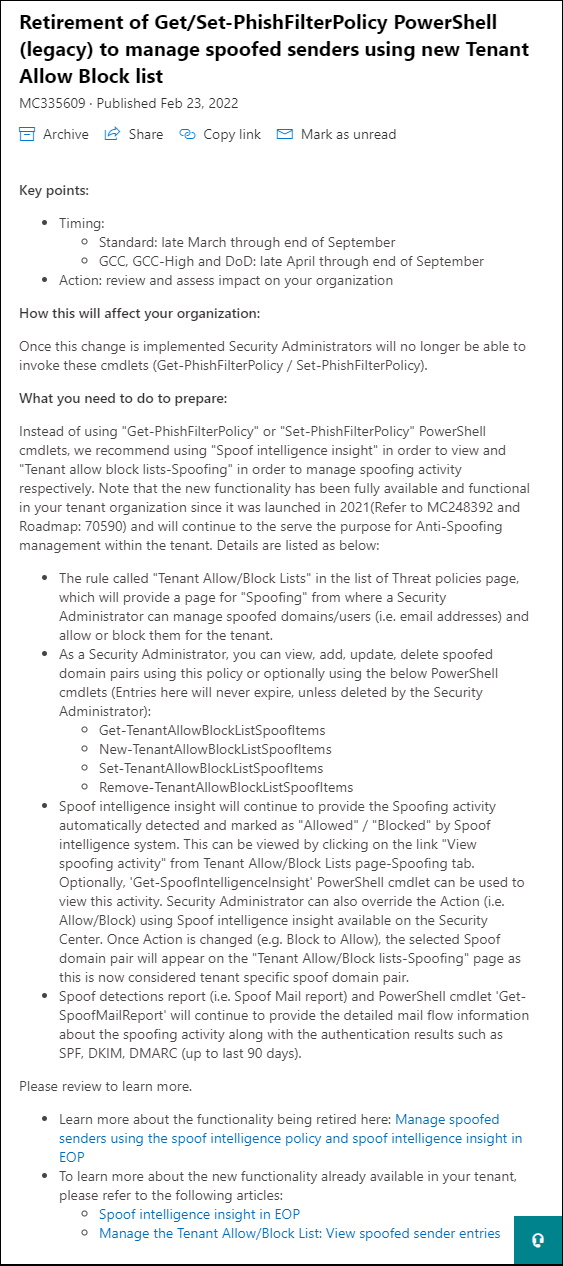
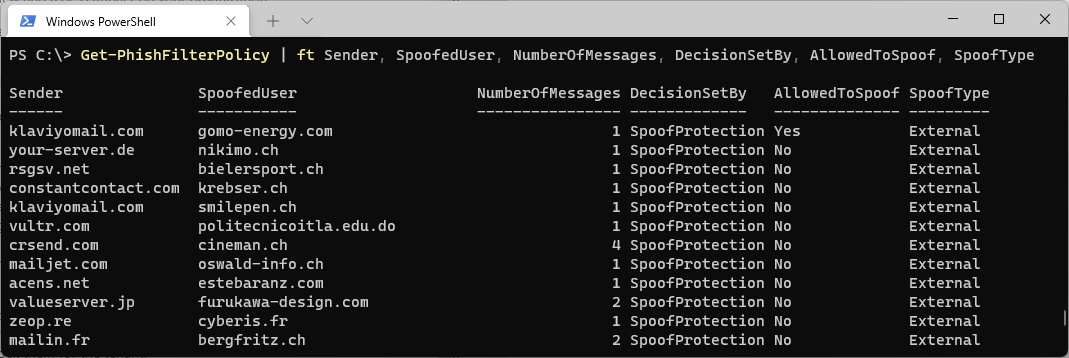
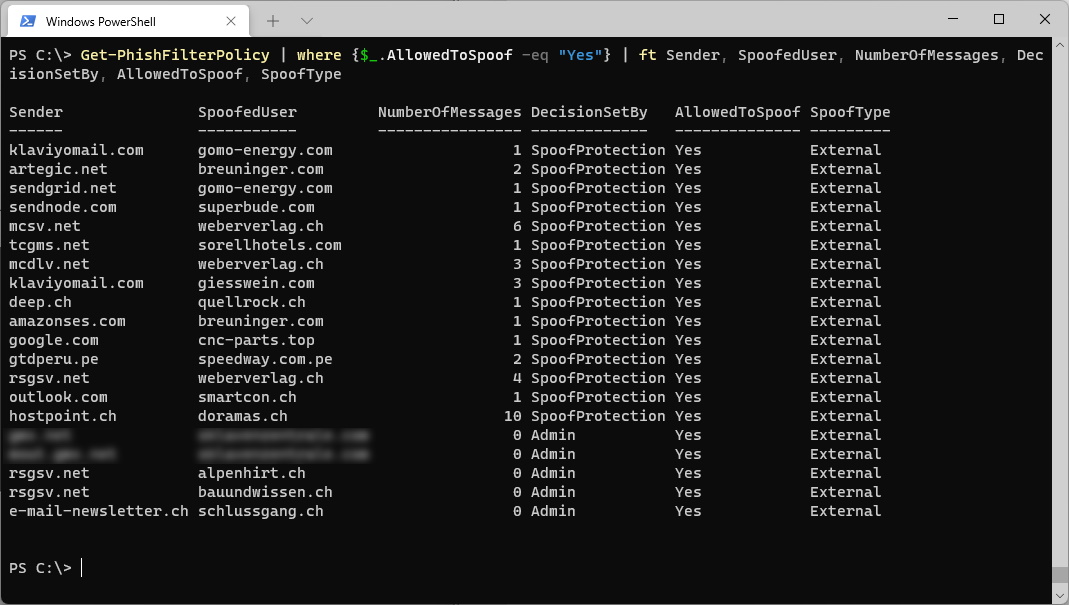
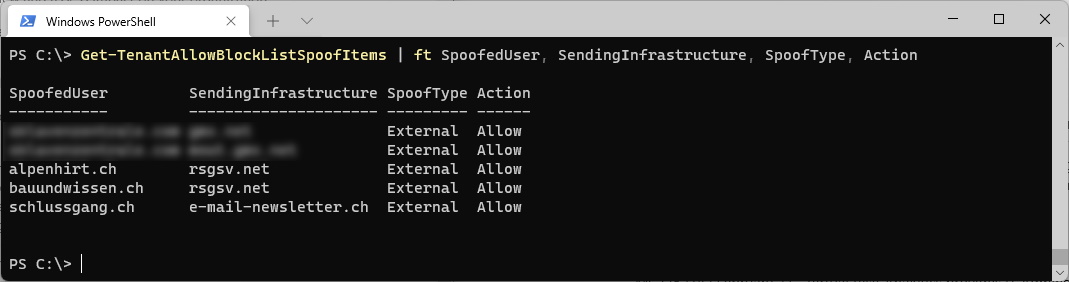
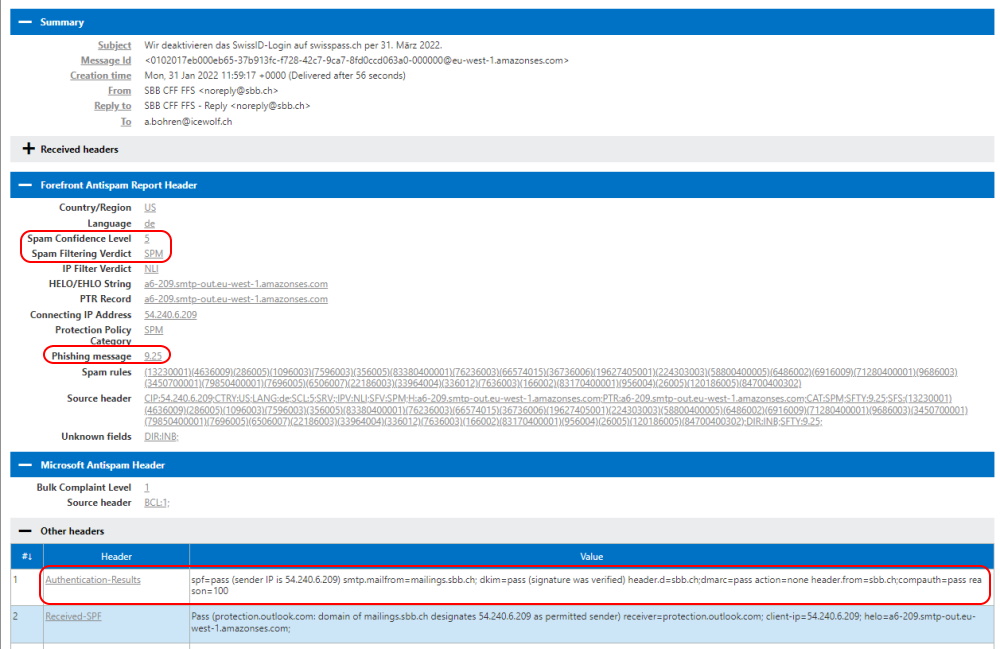
Check for Microsoft Teams Update with PowerShell
Hi All,
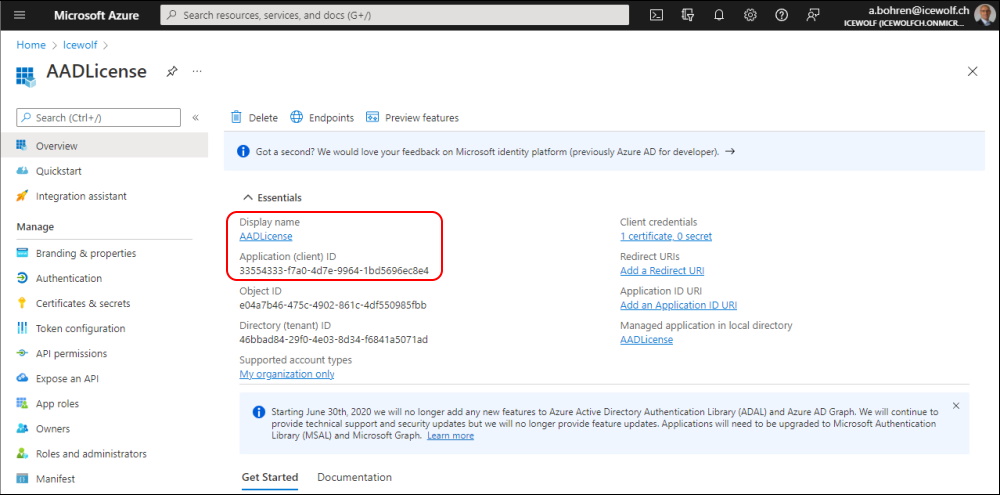
I was inspired to look a little bit deeper into the Update Mechanism of Microsoft Teams by the "Teams MSI Override" GitHub Project.
You can check your Version in Teams by Settings > Info > Version
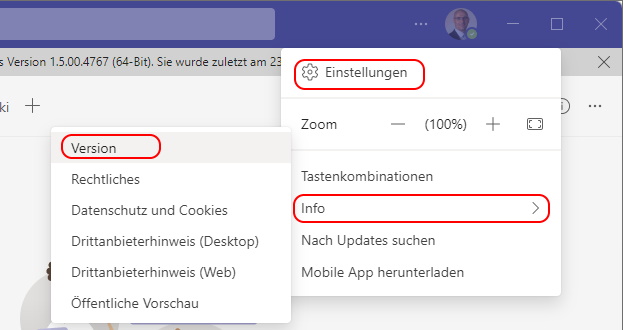
Then the current Version and update Date is shown in the top bar
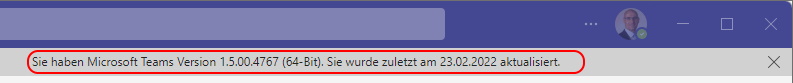
You can invoke a update check in Settings > check for updates
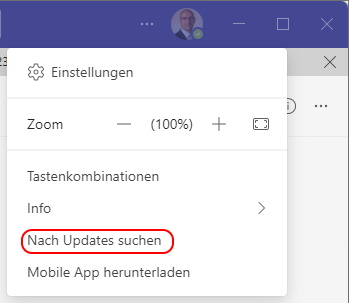
Then Teams will search for updates
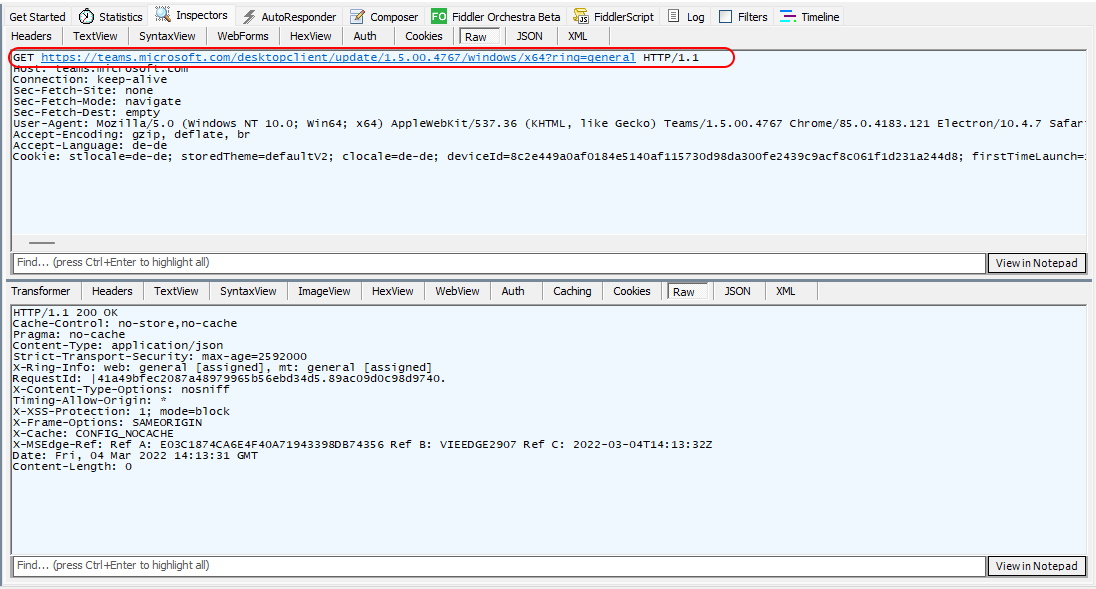
I've traced this Action in Fiddler
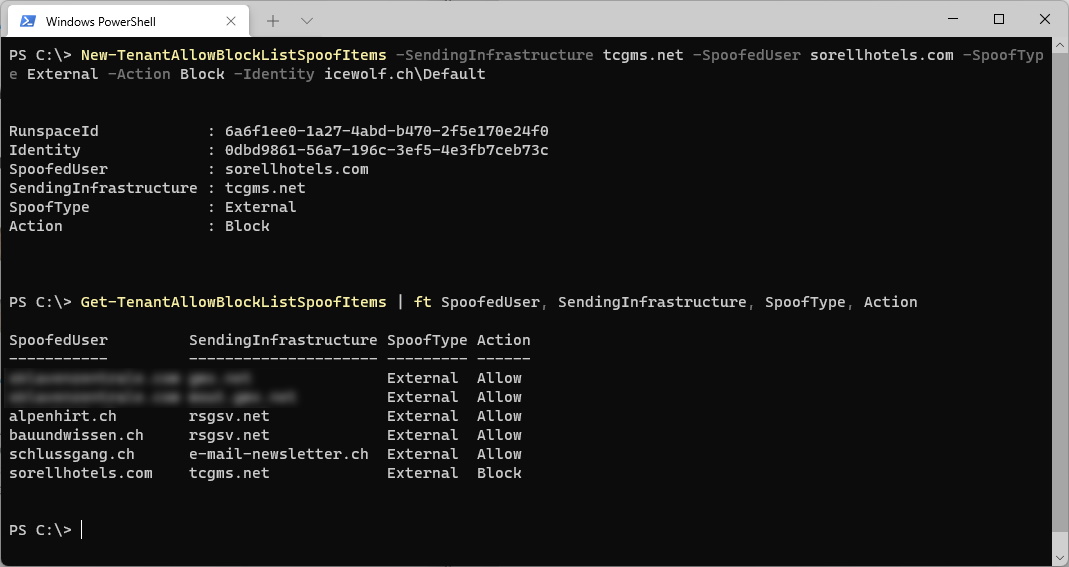
Now you can do your own Check in PowerShell
$Version = "1.5.00.1870"
$Url = "https://teams.microsoft.com/desktopclient/update/$Version/windows/x64?ring=general"
Write-Host "Sending request to $Url"
$updateCheckResponse = Invoke-WebRequest -Uri $Url -UseBasicParsing
$updateCheckJson = $updateCheckResponse | ConvertFrom-Json
$updateCheckJson
$Url = "https://teams.microsoft.com/desktopclient/update/$Version/windows/x64?ring=general"
Write-Host "Sending request to $Url"
$updateCheckResponse = Invoke-WebRequest -Uri $Url -UseBasicParsing
$updateCheckJson = $updateCheckResponse | ConvertFrom-Json
$updateCheckJson
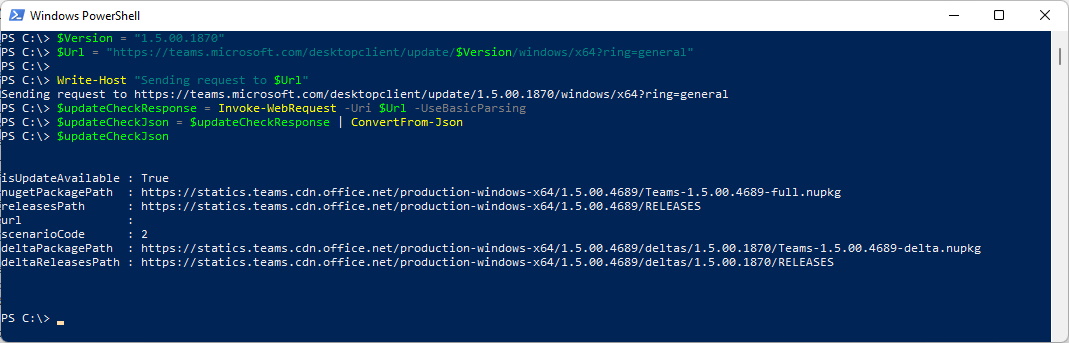
If you send the Current Version you get nothing back - this means there is no update available
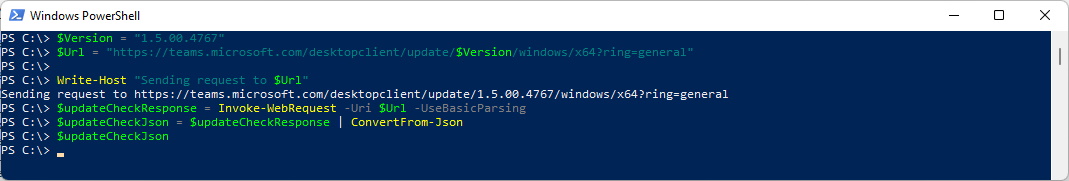
$Version = "1.5.00.4767"
$Url = "https://teams.microsoft.com/desktopclient/update/$Version/windows/x64?ring=general"
Write-Host "Sending request to $Url"
$updateCheckResponse = Invoke-WebRequest -Uri $Url -UseBasicParsing
$updateCheckJson = $updateCheckResponse | ConvertFrom-Json
$updateCheckJson
$Url = "https://teams.microsoft.com/desktopclient/update/$Version/windows/x64?ring=general"
Write-Host "Sending request to $Url"
$updateCheckResponse = Invoke-WebRequest -Uri $Url -UseBasicParsing
$updateCheckJson = $updateCheckResponse | ConvertFrom-Json
$updateCheckJson
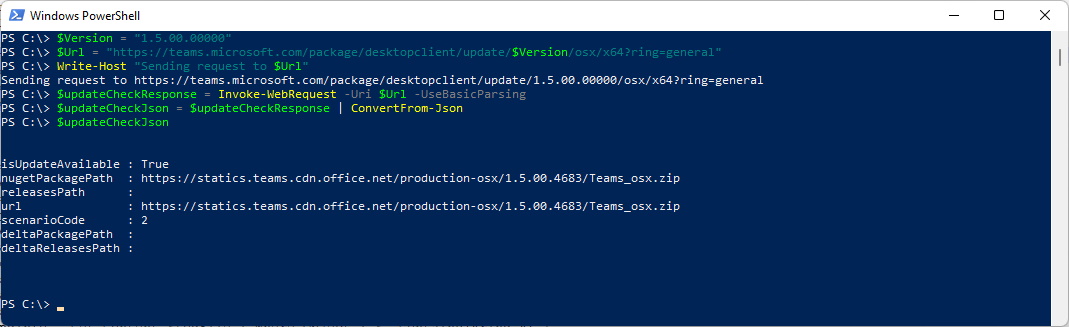
Or you can check for OSX Updates
$Version = "1.5.00.00000"
$Url = "https://teams.microsoft.com/package/desktopclient/update/$Version/osx/x64?ring=general"
Write-Host "Sending request to $Url"
$updateCheckResponse = Invoke-WebRequest -Uri $Url -UseBasicParsing
$updateCheckJson = $updateCheckResponse | ConvertFrom-Json
$updateCheckJson
$Url = "https://teams.microsoft.com/package/desktopclient/update/$Version/osx/x64?ring=general"
Write-Host "Sending request to $Url"
$updateCheckResponse = Invoke-WebRequest -Uri $Url -UseBasicParsing
$updateCheckJson = $updateCheckResponse | ConvertFrom-Json
$updateCheckJson
You might also find some nice Infos the Blog Article from Tom Arbuthnot
Get Microsoft Teams Version, Ring and Install Date with PowerShell
https://tomtalks.blog/get-microsoft-teams-version-powershell/
https://tomtalks.blog/get-microsoft-teams-version-powershell/
Regards
Andres Bohren