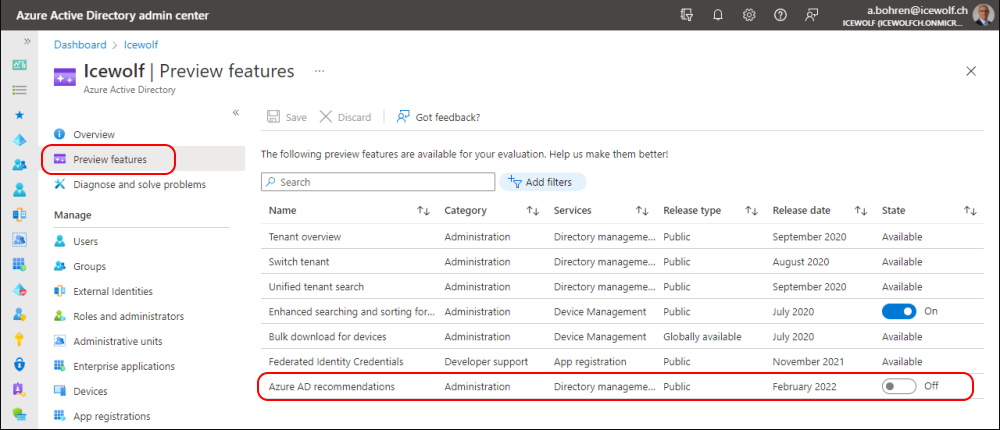
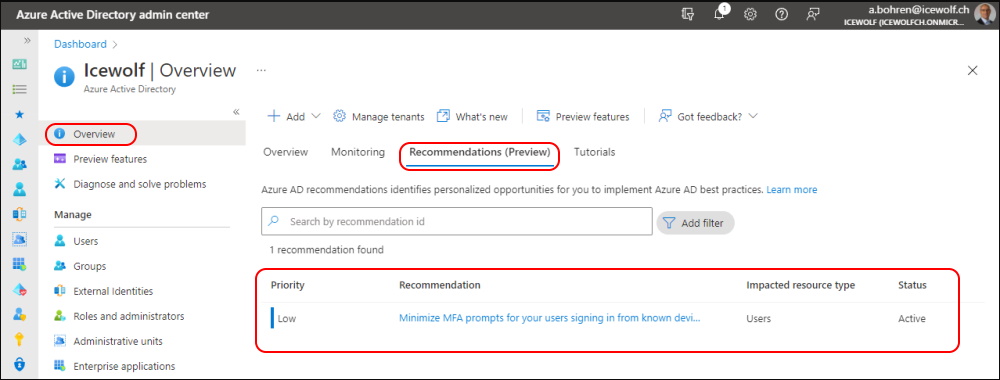
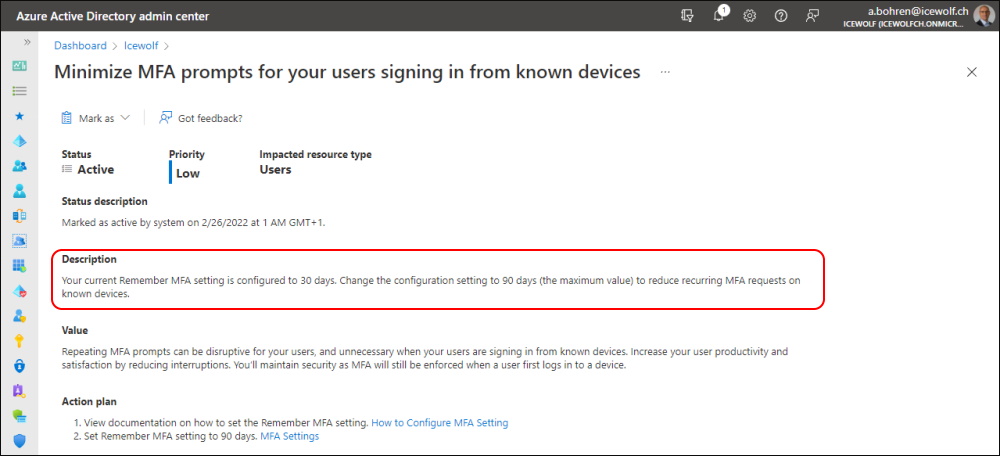
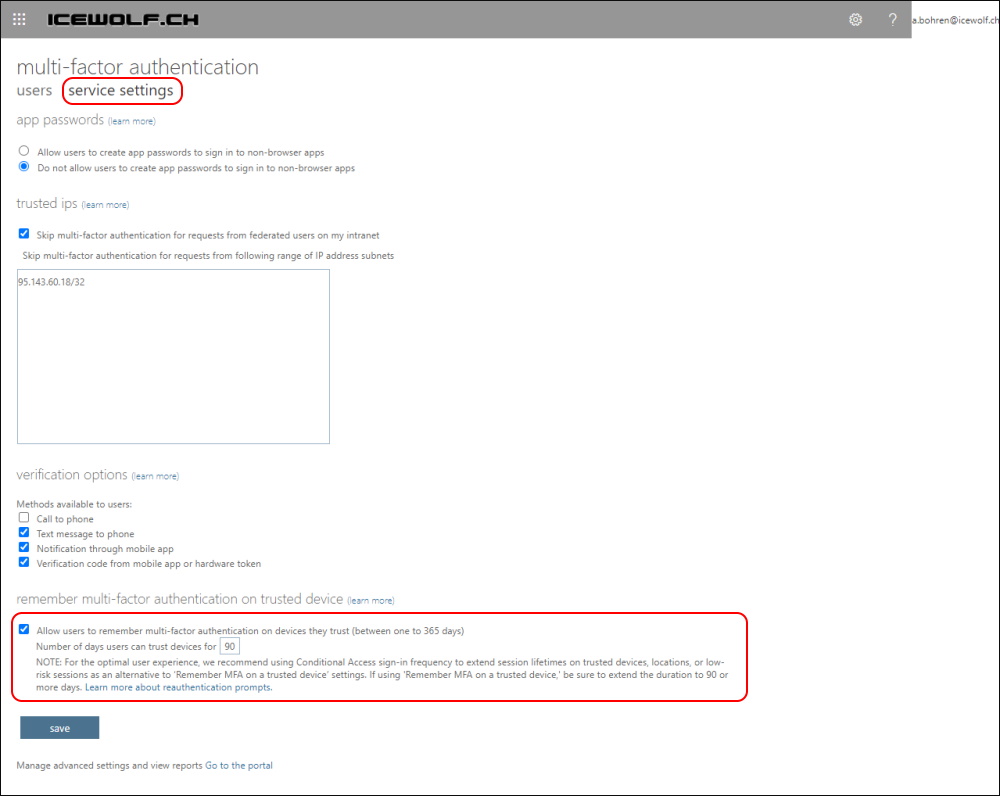
Cleanup Microsoft.Graph PowerShell Modules
Hi All,
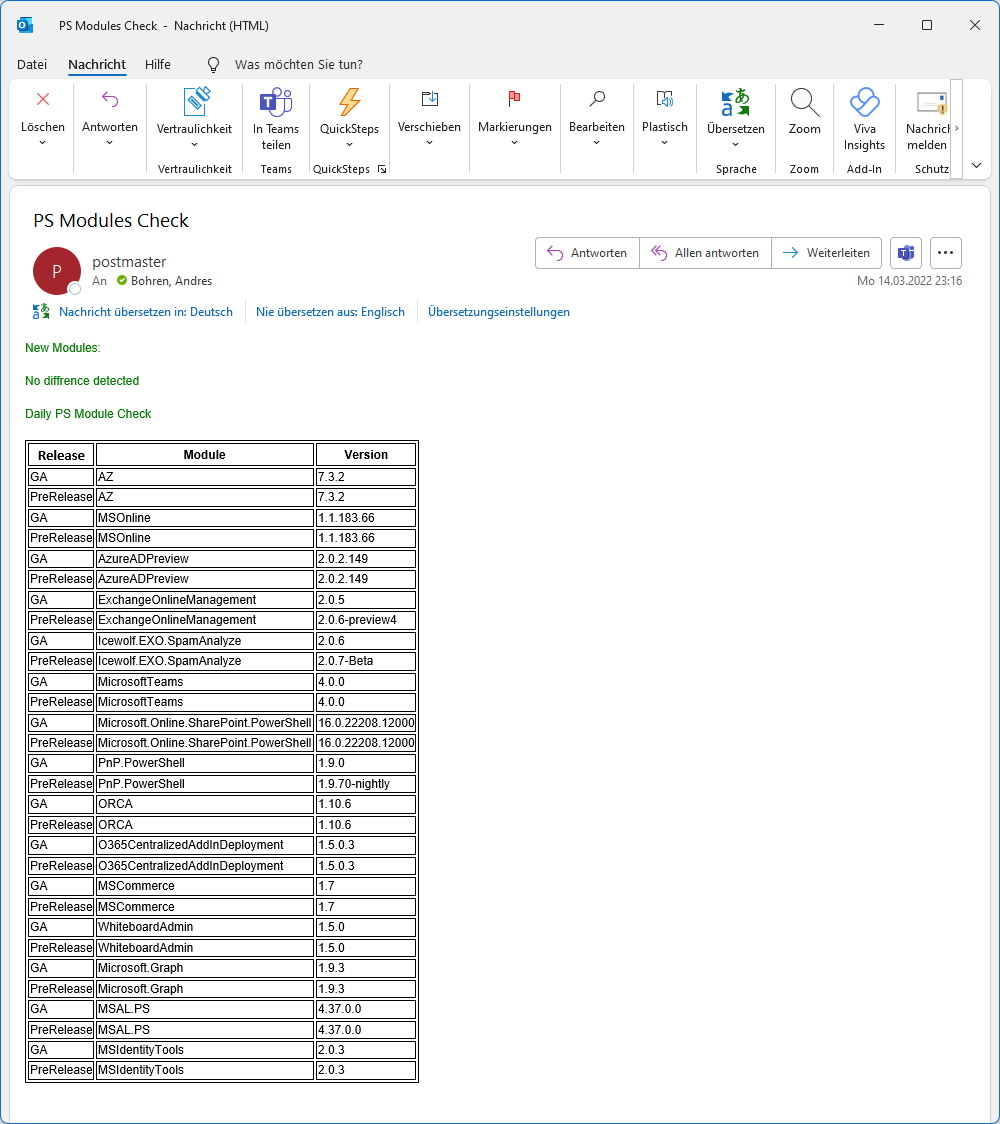
I wanted to check the amount of Commands available in the Microsoft.Graph Powershell Modules
Get-Command -Module Microsoft.Graph* | measure

That seemed a bit much and it turned out, i had multiple Versions of Microsoft.Graph PowerShell Module installed.
Here is a Script do remove the Old Modules and install only the newest Version.
$Modules = Get-Module Microsoft.Graph* -ListAvailable | Where {$_.Name -ne "Microsoft.Graph.Authentication"} | Select-Object Name -Unique
Foreach ($Module in $Modules)
{
$ModuleName = $Module.Name
$Versions = Get-Module $ModuleName -ListAvailable
Foreach ($Version in $Versions)
{
$ModuleVersion = $Version.Version
Write-Host "Uninstall-Module $ModuleName $ModuleVersion"
Uninstall-Module $ModuleName -RequiredVersion $ModuleVersion
}
}
#Uninstall Microsoft.Graph.Authentication
$ModuleName = "Microsoft.Graph.Authentication"
$Versions = Get-Module $ModuleName -ListAvailable
Foreach ($Version in $Versions)
{
$ModuleVersion = $Version.Version
Write-Host "Uninstall-Module $ModuleName $ModuleVersion"
Uninstall-Module $ModuleName -RequiredVersion $ModuleVersion
}
Install-Module Microsoft.Graph
Foreach ($Module in $Modules)
{
$ModuleName = $Module.Name
$Versions = Get-Module $ModuleName -ListAvailable
Foreach ($Version in $Versions)
{
$ModuleVersion = $Version.Version
Write-Host "Uninstall-Module $ModuleName $ModuleVersion"
Uninstall-Module $ModuleName -RequiredVersion $ModuleVersion
}
}
#Uninstall Microsoft.Graph.Authentication
$ModuleName = "Microsoft.Graph.Authentication"
$Versions = Get-Module $ModuleName -ListAvailable
Foreach ($Version in $Versions)
{
$ModuleVersion = $Version.Version
Write-Host "Uninstall-Module $ModuleName $ModuleVersion"
Uninstall-Module $ModuleName -RequiredVersion $ModuleVersion
}
Install-Module Microsoft.Graph
Now let's check again
Get-Module Microsoft.Graph* -ListAvailable
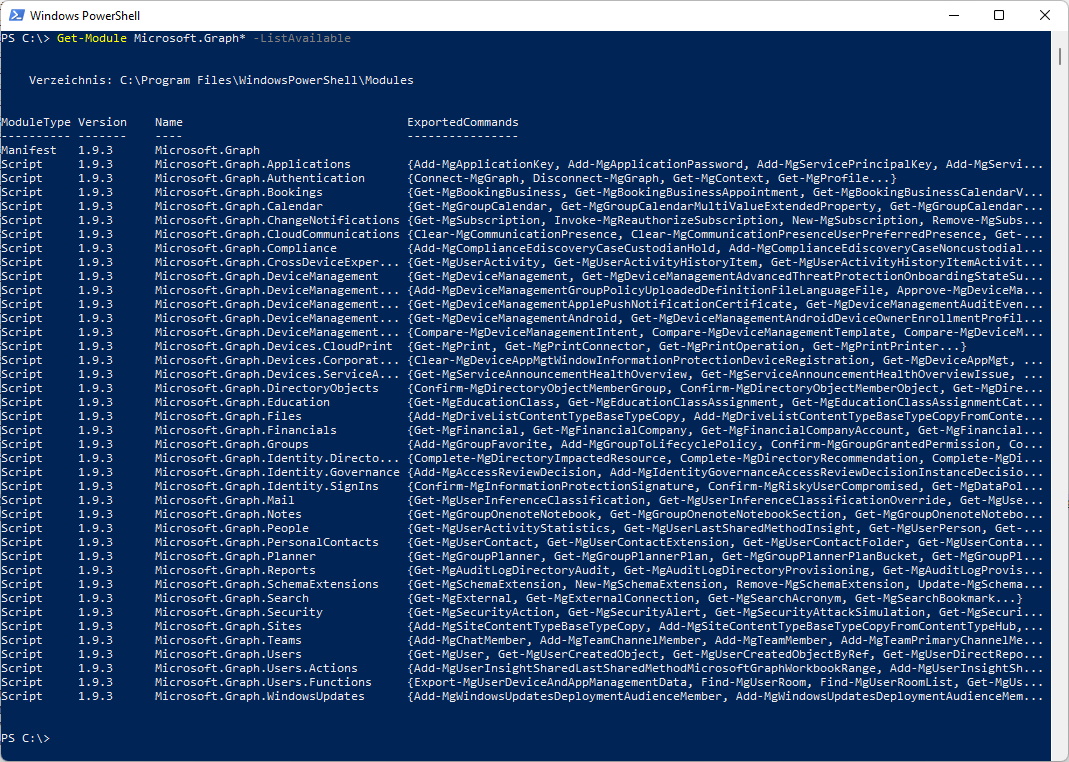
When i check now for the available commands it looks more sensable
Get-Command -Module Microsoft.Graph* | measure

Regards
Andres Bohren