Use Managed Identity with Exchange Online on Azure Automation
Hi All,
With the ExchangeOnlineManagement PowerShell Module 3.0.0, Microsoft has providet the Ability to use Managed Identity in Azure. Time to test that on my own.
v3.0.0 :
-
General Availability of REST-backed cmdlets for Exchange Online which do not require WinRM Basic Authentication to be enabled.
-
General Availability of Certificate Based Authentication for Security and Compliance PowerShell cmdlets.
-
Support for System-Assigned and User-Assigned ManagedIdentities to connect to ExchangeOnline from Azure VMs, Azure Virtual Machine Scale Sets and Azure Functions.
I will use an Azure Automation Account. As i have already used that for Automation with Exchange. That Time with OAuth Authenication with a Certificate to Exchange Online.
-
Use Azure Automation for Exchange Online PowerShell Script - Part 1
-
Use Azure Automation for Exchange Online PowerShell Script - Part 2
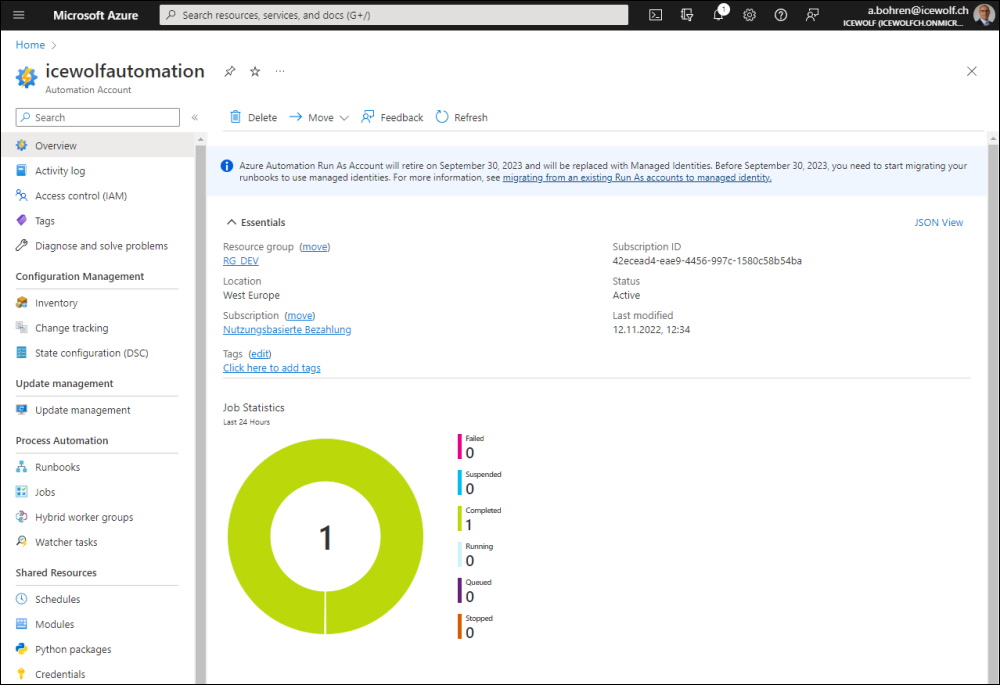
To view the Azure Automation Account with Powershell i use the AZ PowerShell Module.
#Connect to Azure
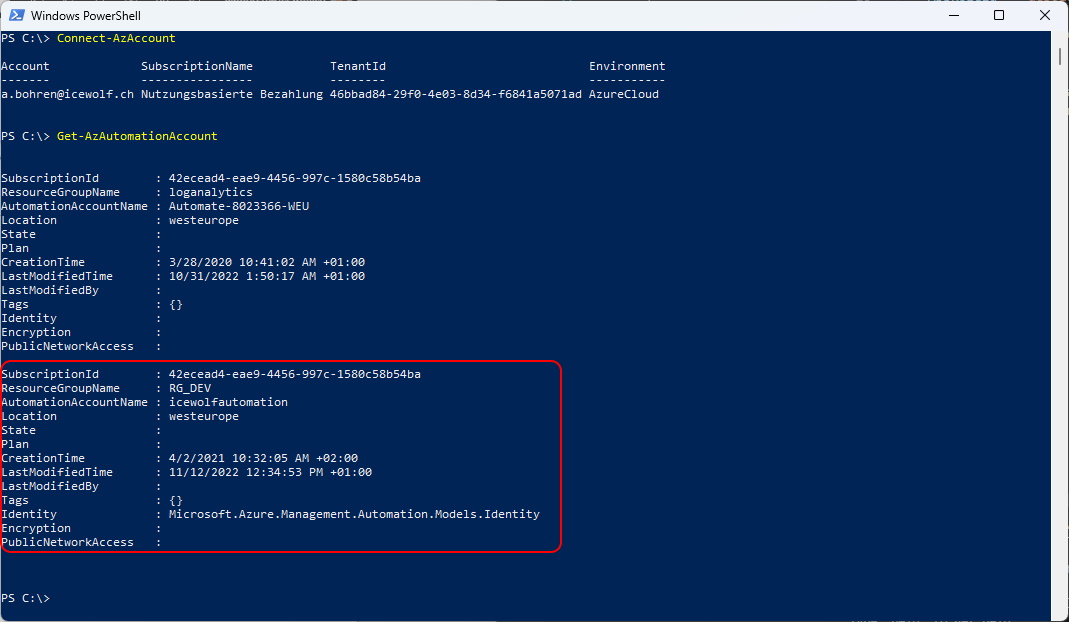
Connect-AzAccount
#Get Automation Account
Get-AzAutomationAccount
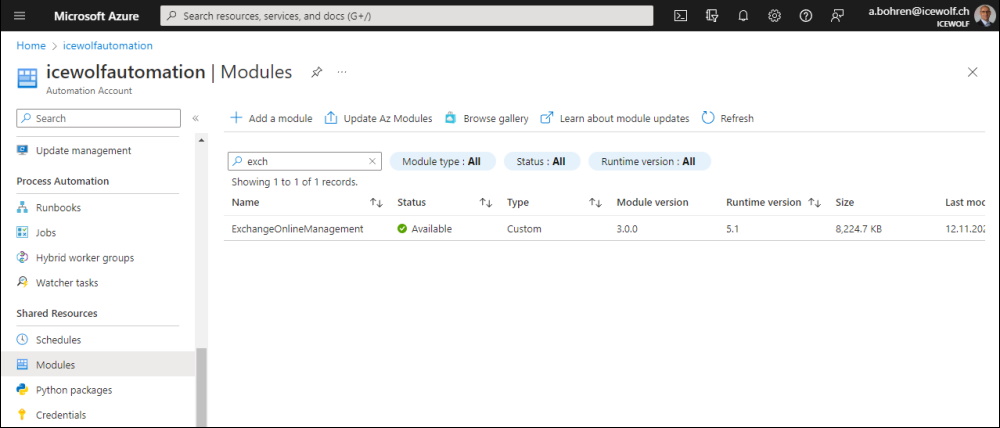
Make sure you have the ExchangeOnlineManagement PowerShell Module 3.0.0 installed
You can check this with the following Command
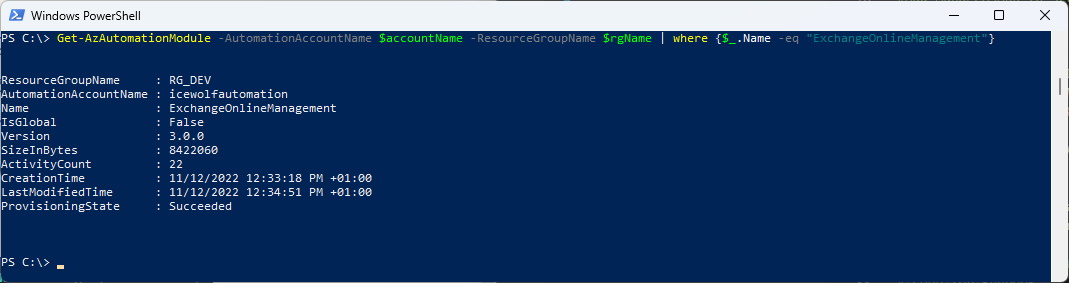
#Check AzAutomation Module
$accountName = 'icewolfautomation'
$rgName = 'RG_DEV'
Get-AzAutomationModule -AutomationAccountName $accountName -ResourceGroupName $rgName | where {$_.Name -eq "ExchangeOnlineManagement"}
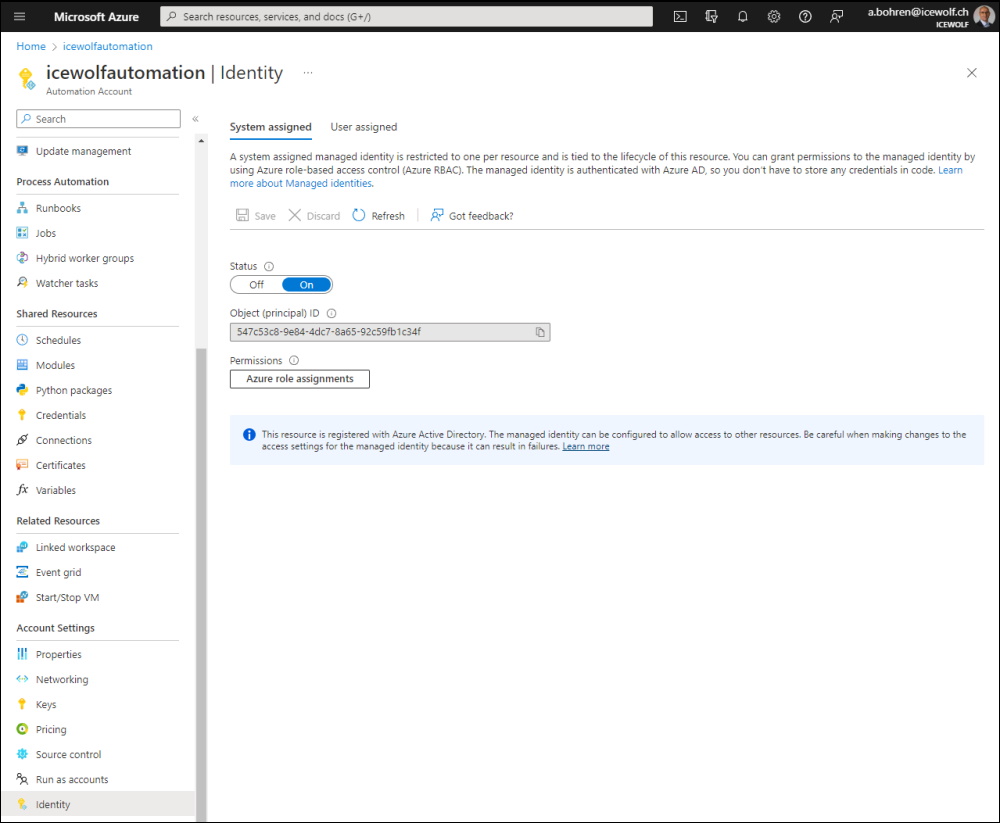
I have already created the System assigned Managed Identity
Check the Identity
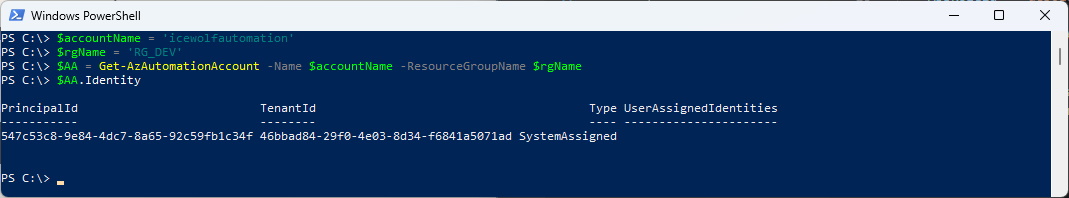
#Get Specific Automation Account
$accountName = 'icewolfautomation'
$rgName = 'RG_DEV'
$AA = Get-AzAutomationAccount -Name $accountName -ResourceGroupName $rgName
$AA.Identity
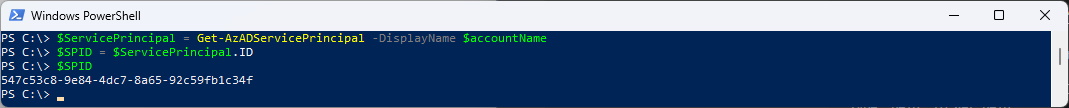
Or use this command
#Get Service Principal
$ServicePrincipal = Get-AzADServicePrincipal -DisplayName $accountName
$SPID = $ServicePrincipal.ID
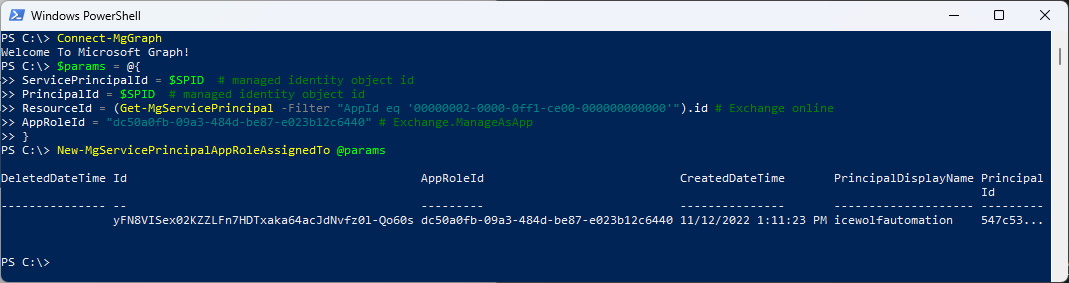
As already explained in the Article below, you need to add the App (Service Principal) to the “Exchange Administrators Role” and assign the “Exchange.ManageAsApp” Permission.
#Add ManageAsApp to Service Principal
Connect-MgGraph
$params = @{
ServicePrincipalId = $SPID # managed identity object id
PrincipalId = $SPID # managed identity object id
ResourceId = (Get-MgServicePrincipal -Filter "AppId eq '00000002-0000-0ff1-ce00-000000000000'").id # Exchange online
AppRoleId = "dc50a0fb-09a3-484d-be87-e023b12c6440" # Exchange.ManageAsApp
}
New-MgServicePrincipalAppRoleAssignedTo @params
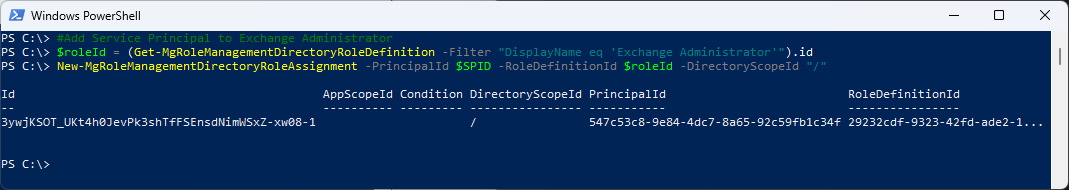
#Add Service Principal to Exchange Administrator
$roleId = (Get-MgRoleManagementDirectoryRoleDefinition -Filter "DisplayName eq 'Exchange Administrator'").id
New-MgRoleManagementDirectoryRoleAssignment -PrincipalId $SPID -RoleDefinitionId $roleId -DirectoryScopeId "/"
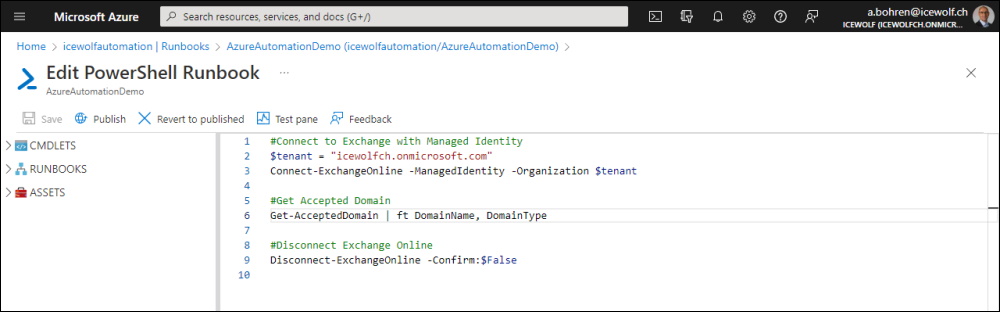
Here is my code for the Azure Automation Runbook
###############################################################################
# Code for Azure Automation Runbook
###############################################################################
#Connect to Exchange with Managed Identity
$tenant = "icewolfch.onmicrosoft.com"
Connect-ExchangeOnline -ManagedIdentity -Organization $tenant
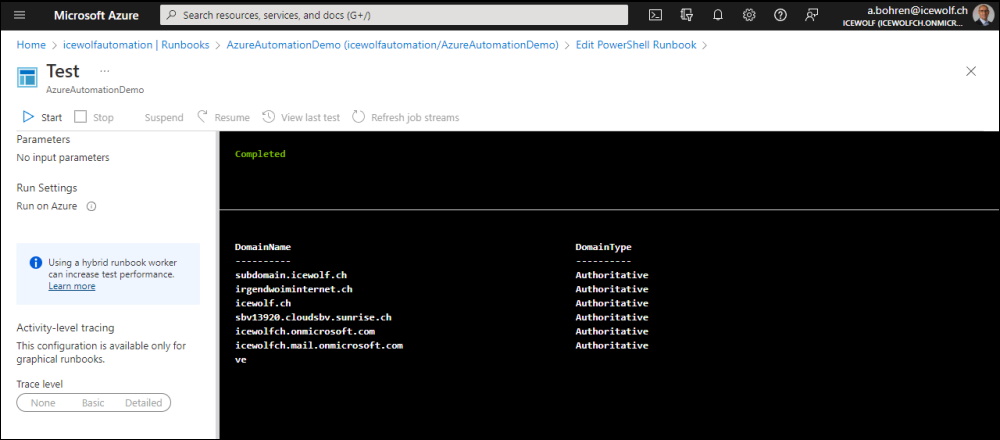
#Get Accepted Domain
Get-AcceptedDomain | Format-Table DomainName, DomainType
#Disconnect Exchange Online
Disconnect-ExchangeOnline -Confirm:$False
Regards
Andres Bohren